The Department of National Security: The main despicable means of cyber attacks and theft by US intelligence agencies during the uprising
Recently, China's National Computer Virus Emergency Response Center reported that it successfully extracted a spy software sample called "Second Date" while dealing with a network attack on Northwestern Polytechnical University. This software is a network "spy" weapon developed by the National Security Agency of the United States, which operates secretly in thousands of network devices spread across multiple countries around the world.
The United States is notorious in the field of cybersecurity. In a series of US espionage and intelligence agency cyber attacks and espionage cases uncovered by national security agencies, the despicable tactics of the "hacker empire" to maintain "cyber hegemony" have surfaced.
Tip 1: Establish a cyber attack arsenal
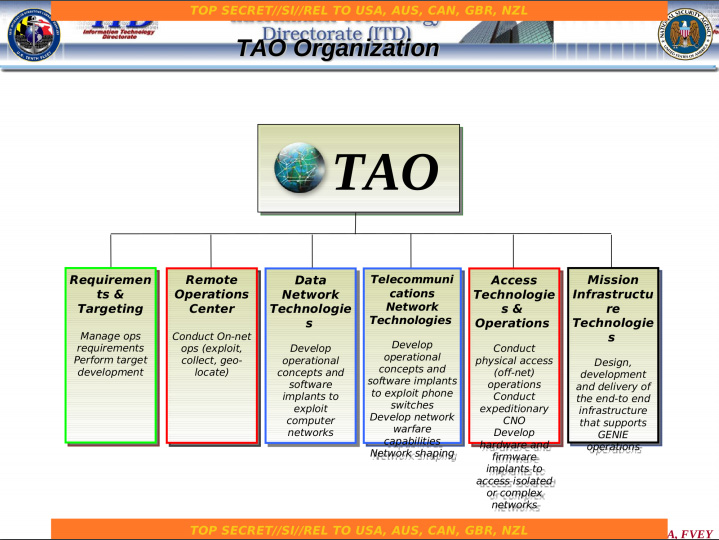
The US intelligence agency, with its powerful arsenal of cyber attack weapons, has carried out surveillance, espionage, and cyber attacks on multiple countries around the world, including China, to the utmost extent possible. Especially the National Security Agency of the United States, through its specific intrusion operations office and advanced weapon arsenal, has repeatedly carried out systematic and platform based attacks on our country, attempting to steal important data resources from our country.

US National Security Agency Headquarters
In 2009, specific intrusion action offices began to invade Huawei headquarters servers and continued to monitor them. In September 2022, it was discovered that tens of thousands of malicious network attacks had been carried out on domestic network targets, including Northwestern Polytechnical University, for a long time, controlling tens of thousands of network devices and stealing a large amount of high-value data.
The US intelligence agency's ability to launch large-scale cyber attacks naturally relies on diverse cyber attack weapons as a backing. Since 2022, China's cybersecurity agencies have disclosed multiple US intelligence agency cyber attack weapons, such as Operation Electric Curtain, Quantum, Sour Fox, and Beehive. The US intelligence agency has used these large-scale weapons and equipment to carry out more than a decade long cyber attacks and espionage operations against 45 countries and regions around the world, including China and Russia. The cyber attack targets include core important fields such as telecommunications, scientific research, economy, energy, and military.
Tip 2: Force relevant technology companies to cooperate through backdoors
The US government, citing national security concerns, has enforced backdoors in the devices, software, and applications of related technology companies through laws such as the Foreign Intelligence Surveillance Act. By using embedded code, vulnerability attacks, and leveraging the influence of its global technology companies, it can monitor and steal global data.
In December 2020, X-Mode Social, a US location data company, was exposed for obtaining location data through software development toolkits built into applications and selling the data to contractors closely related to the US military and intelligence agencies. In April 2022, Anomaly Six, a company with a US military intelligence background, was exposed for embedding its internal tracking software development package into numerous mobile applications to track the location data and browsing information of hundreds of millions of mobile phones worldwide, and consolidating and selling this data to the US government.
Tip Three: Invert Black and White, Thieves Shout to Catch Thieves
On the one hand, the United States is vigorously carrying out cyber attacks and secret theft against countries around the world, while on the other hand, it is concocting various versions of "security reports", smearing China as the "subject of cyber threats", exaggerating and hyping up the so-called "China's cyber theft" problem, and portraying "reversing black and white" as a pure fire.

As is well known, the United States has long relied on its technological advantages to conduct large-scale eavesdropping and cyber espionage activities on countries around the world, including allies, which has long been an open secret. Since the Prism Gate incident was exposed in 2013, relevant cybersecurity agencies in China have repeatedly discovered the presence of the United States in cyber attacks targeting China. In recent years, the United States has intensified its "forward hunting" campaign, which has clear objectives, with Russia, Iran, China, and North Korea as its main targets. The US Cyberspace Command is becoming an expeditionary force, using the guise of "going hunting" and active defense to carry out cyber attacks and espionage against other countries.
However, at the same time, the United States vigorously portrays itself as a "victim of cyber attacks", advocating and coercing other countries to join the so-called "clean network" plan under the guise of "maintaining cybersecurity", attempting to eliminate Chinese companies in the international online market. In fact, "cleaning the internet" is fake, suppressing opponents and maintaining hegemony is real. In response to this, Chinese officials have repeatedly urged the United States to deeply reflect, stop global cyber attacks and theft, and stop confusing the public with various false information.
Currently, cyberspace is increasingly becoming a new battlefield for maintaining national security. Without cybersecurity, there would be no national security, no stable economic and social operation, and the interests of the general public would be difficult to safeguard. Let's join hands, strengthen security awareness, enhance security capabilities, and jointly maintain network security.