Why did the United States attack China's earthquake monitoring center? Monitoring Center | Earthquake | United States
This morning, Tan Zhu noticed an unusual news:
The Jianghan Branch of Wuhan Public Security Bureau in Hubei Province has issued a police report stating that some network devices of the Earthquake Monitoring Center of Wuhan Emergency Management Bureau have been implanted with Trojan viruses. It is preliminarily determined that this incident was a network attack initiated by foreign hacker organizations and criminals with government background.
I believe many people, like Tan Zhu, have some doubts when they see this news. Isn't a lot of earthquake data publicly available? Why do foreign hacker organizations and criminals attack an earthquake monitoring center? Where do they come from?
Tan Zhu contacted the Wuhan Emergency Management Bureau, who stated that the National Computer Virus Emergency Response Center and 360 Company have conducted traceability analysis on the Trojan virus. We learned from these two institutions that this overseas hacker organization is from the United States.
It's the United States again. The United States is launching a cyber attack on China's earthquake monitoring center. What are you trying to do?
With this question in mind, Tan Zhu chatted with a professional.
He stated that seismic waves passing through different underground media and structures can cause changes in wave velocity. Obtaining relevant data from the earthquake monitoring center can deduce the underground structure and lithology of a certain area. For example, speculate whether there are large voids underground, and then speculate whether it is a military base or command post.
He gave Tan Zhu an analogy, it's like going out alone after dinner and hearing various sounds. Putting these sounds together at the same time may feel very noisy, it's noise. But by analyzing these sounds in the simplest way possible, you will come up with a lot of information - the sound of wind, the sound of cars.
What is the purpose of the United States launching this cyber attack to analyze? Tan Zhu decided to start with American intelligence agencies and search for clues.
Many people are familiar with American intelligence agencies, such as the Federal Bureau of Investigation, the Central Intelligence Agency, and the National Security Agency.
But in reality, these agencies are just the tip of the iceberg in the US intelligence system. Currently, there are 18 intelligence agencies in the US:
These 18 institutions are affiliated with different departments in the United States and jointly weave an intelligence network.
Among them, the Central Intelligence Agency and the National Security Agency are habitual perpetrators of cyber attacks.
Last year, Northwestern Polytechnical University in China was attacked by the National Security Agency of the United States. More than two months ago, Tan Zhu also made an exclusive interpretation of how close the real version of the "Matrix" is to us, detailing how the Central Intelligence Agency of the United States carried out destructive operations online.
It is highly likely that cyber attacks were initiated by these two departments. In the US scenario, if this data is obtained, who will do the analysis work?

Based on the US cyber attack on the earthquake monitoring center, Tan Zhu sorted out the functions of these 18 intelligence agencies and then focused on one agency - the US Defense Intelligence Agency.
The US Defense Intelligence Agency, as a foreign military intelligence agency under the US Department of Defense, has confidential information on its number of employees and budget.
The recent report related to it is that DIA established a "China Task Force" at the end of last year, which convened a group of analysts and experts to provide DIA with a "toolbox" specifically for China.
In addition, DIA will regularly release the "China Military Power Report", which is of great significance for the United States to formulate military policies towards China.
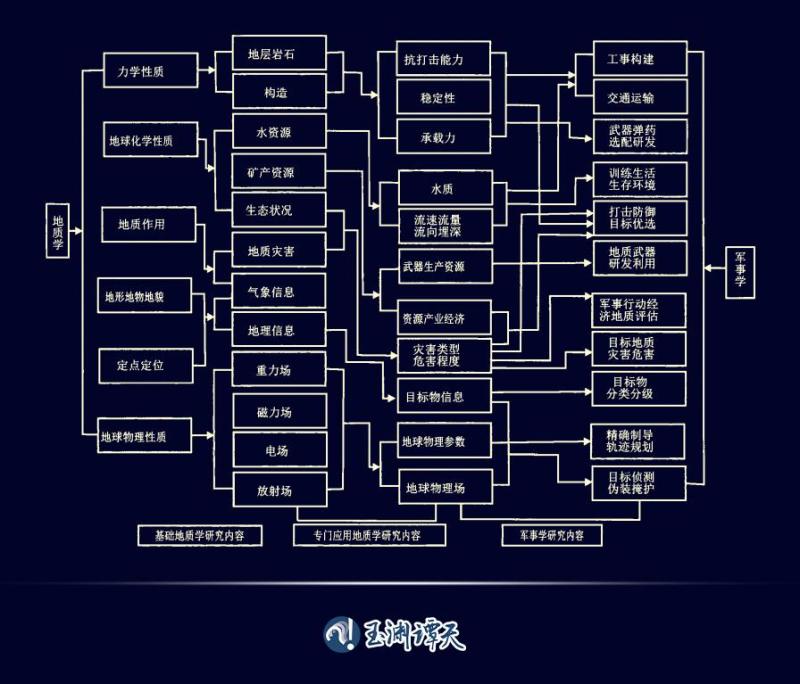
Besides, there is not much information about DIA. But after carefully examining the development process and organizational structure of DIA, we found that DIA also has a function - military geological research.
From this picture, it can be seen that there is a strong correlation between geology and military affairs.
The Gulf War, known as the boundary between modern and traditional warfare, saw the US military deploy a large number of high-tech weapons in actual combat, demonstrating overwhelming advantages on the battlefield.
At that time, many people focused their attention on the United States' air superiority, and few paid attention to another factor - the US military's geological and terrain intelligence.
Before launching the war, the US military conducted a large-scale acquisition and analysis of geological data from Iraq, and determined that the Iraqi command center was hidden 30 meters underground. In addition, the US military also conducted a geological analysis of the rock formations at the location of the center.
At the beginning of the war, the US military launched laser guided ground penetrating bombs with geological information chips, directly destroying the Iraqi military's command structure.
Seeing this, looking back at the network attack on the Wuhan earthquake monitoring center, is it a bit scary and thoughtful?
With the continuous development of war forms, the boundary between civilian and military facilities is becoming increasingly blurred, and precise strikes are becoming increasingly important.
To achieve precise strikes, more geological and terrain information is needed as support.
In order to obtain this information, US intelligence agencies have increased their efforts in cyber attacks and cyber theft. Currently, the United States has developed a complete set of cyber attack weapons and equipment that can attack global targets at will.
According to relevant reports, the United States has conducted multiple simulated strike tests on over 10000 key underground targets worldwide using its current geological intelligence, providing important references for precise strikes.
With the development of geology in our country, the data monitored by earthquake monitoring centers will become increasingly multidimensional. This also means that once this information is leaked, more information can be analyzed.
Professionals say that the monitoring center will also simultaneously monitor information such as groundwater level and soil.
Tan Zhu noticed that the US Defense Intelligence Agency began studying the impact of soil on military operations several years ago, and related research has been subdivided into what effects soil moisture content and temperature will have on military vehicle traffic.
As the US national security strategy defines China as a "strategic competitor," major US intelligence agencies have also adjusted their primary task to help the US succeed in strategic competition with China.
On the wall of the headquarters of the US Defense Intelligence Agency, there is a sentence that says, "Pay attention to the opinions, comments, and jokes of the general public.". This sentence is a reminder to themselves that any subtle data and information has great value.
Now, the US Defense Intelligence Agency holds such an attitude, staring at China, hoping to obtain China's information through illegal means such as cyber attacks, and formulate plans against China.
The cyber attack weapons studied by US intelligence agencies have penetrated into various industries:
The hacker programs studied by the Central Intelligence Agency in the United States can specifically target smart TVs, and the over a thousand hacker systems they manufacture can almost cover the vast majority of electronic device systems on the current market;
The Office of Specific Intrusion Operations, a subsidiary of the US National Security Agency, studies how to remotely invade car computer systems to assassinate specific targets;
The move by the United States to attack the earthquake monitoring center indicates that the next step for US cyber attacks is to penetrate into daily and daily life.
Cyber attacks may seem distant from ordinary people, but when the United States develops cyber attack weapons, it consciously combines areas closely related to ordinary people. Once it launches a cyber attack, it will also affect ordinary people.
Faced with such enemies, what we need to do is not only to improve our protective capabilities, but also to weave a protective "sky net" through interdisciplinary and cross domain collaboration.




