Whoever is leaking student information can buy 200 pieces of personal information for 1 yuan | Information | Students
When personal information is used for beauty rating, people in the era of information streaking are once again angry.
Recently, Ma, a graduate of Renmin University of China, was suspected of illegally accessing the school's internal network data during his time at school, collecting personal privacy information of all students, and publicly posting it on the website for appearance rating. At present, the Haidian police in Beijing have lawfully detained Ma, and the case is under further investigation.
When the incident was exposed, the first reaction of Xiao Lin, a student at Renmin University of China, was surprise: "How did he obtain this data? Where did he obtain it?" Along with it came anger and disgust at being offended.
Pengpai News has sorted out 52 judgment documents related to the leakage of personal information of students in the past three years, attempting to explore who is leaking student information, which links have gone wrong, and who should be responsible for it?
Cheap personal information: 1 yuan can buy information for 200 students
These 52 judgments reveal the crimes and punishments related to the leakage of personal information of students.
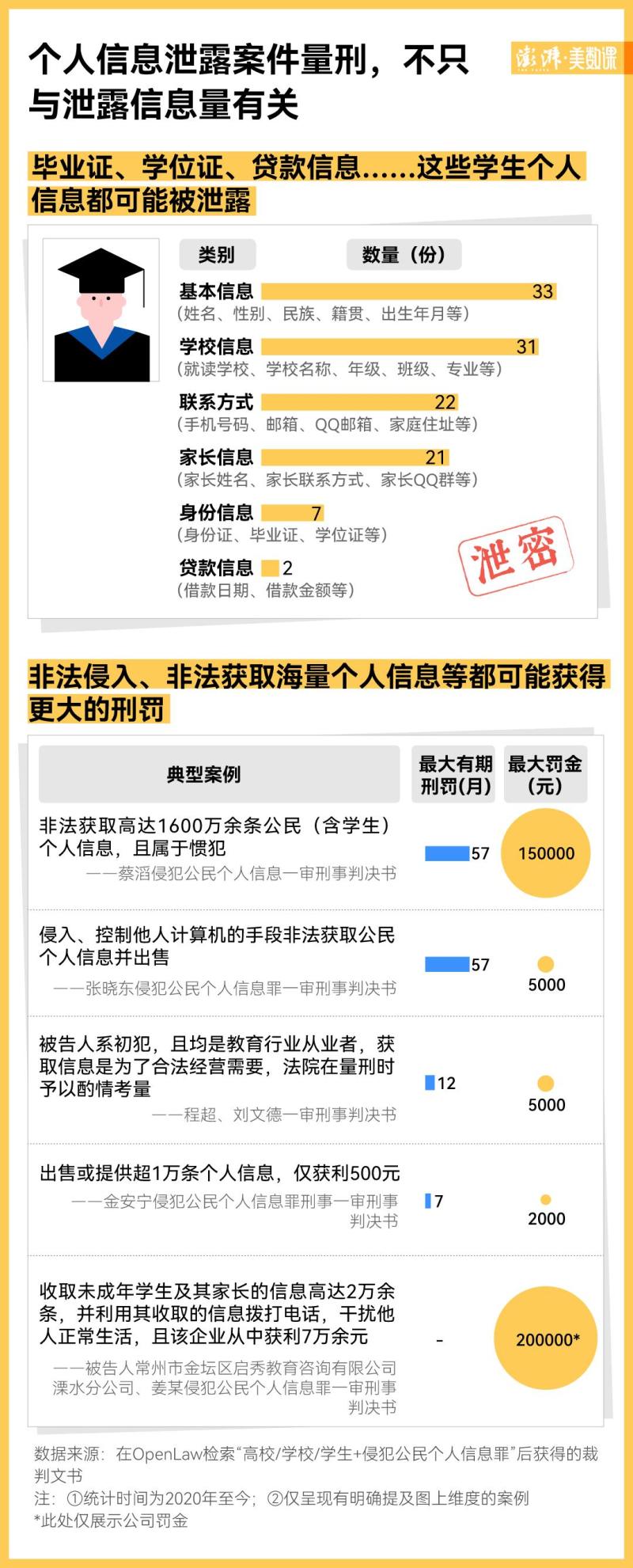
39 identified the main types of information leakage - personal basic information and school information are the most common types of information leakage, including name, gender, date of birth, school, major, class, etc. In addition, criminals also obtained more sensitive personal information such as ID cards and loan information.
In addition to personal information related to students, the leakage of information from student groups often accompanies the "naked running" of personal information from parents. According to incomplete statistics, 53% of student information leakage cases involve personal information leakage from parents.
And the unit price of these personal information is extremely low. According to the Criminal Judgment of the First Instance of Wang's Infringement of Citizen Personal Information, criminals can buy 180000 pieces of student information for only 1000 yuan, which is equivalent to buying information for 200 people for only 1 yuan.
After the leakage and combination of different types of personal information, they become the "raw materials" for further infringement by criminals. And these infringements often appear in the form of telecommunications fraud.
In the case tried by the People's Court of Huishan District, Wuxi City, Jiangsu Province in 2020, the defendant Wang Yiheng used personal information and QQ numbers of student parents purchased online in advance, used forged training notices, impersonated their children's identities, and repeatedly deceived the victim of a total of RMB 76120 in money, citing the need to pay training fees. The verdict shows that the defendant Wang Yiheng committed crimes such as fraud and infringement of personal information of citizens, and was sentenced to four years and three months in prison with a fine of 5000 yuan. Among them, those who commit the crime of infringing on the personal information of citizens shall be sentenced to three months' imprisonment and fined 3000 yuan.
By reviewing the sentencing standards of multiple judgments, it can be seen that in the punishment of the crime of infringing on personal information of citizens, various factors such as the volume of information leakage, criminal methods, and criminal purposes will be considered.
Comparing the two judgments, Cai Tao's Criminal Judgment for Infringing Citizen Personal Information in the First Instance and Zhang Xiaodong's Criminal Judgment for Infringing Citizen Personal Information in the First Instance, it can be seen that each defendant was sentenced to 4 years and 9 months of imprisonment, but there was a significant difference in the amount of personal information involved in the case.
The Cai Tao case involves infringing on 16.03 million pieces of personal information of citizens and illegally profiting 38000 yuan; The Zhang Xiaodong case involves the infringement of 279000 pieces of personal information of citizens and illegal profits of 238 US dollars. The court pointed out that due to the use of methods such as intrusion and control of others' computers in the illegal acquisition of personal information by Zhang Xiaodong, the circumstances are particularly serious, and the sentencing is heavier than other similar cases where the amount of personal information leakage and profits of citizens are obtained.
Expert: Enterprises and other units should establish and implement data compliance systems
It is currently unclear how Ma obtained the school's intranet data. In previous cases, many criminals obtained a large amount of personal information of students through the convenience of their positions. At least one-third of the 52 judgment documents are in this type of situation.
A case that has been reported by multiple media outlets is that students from multiple universities in Chengdu suddenly discovered that they were "employed" and that some companies had stolen their identity information for tax evasion. The source of information leakage is that an employee of an insurance company leaked the list of student information they obtained while working.
The above cases all tell us that the vulnerability of student information leakage often lies in the employees who come into contact with the data.
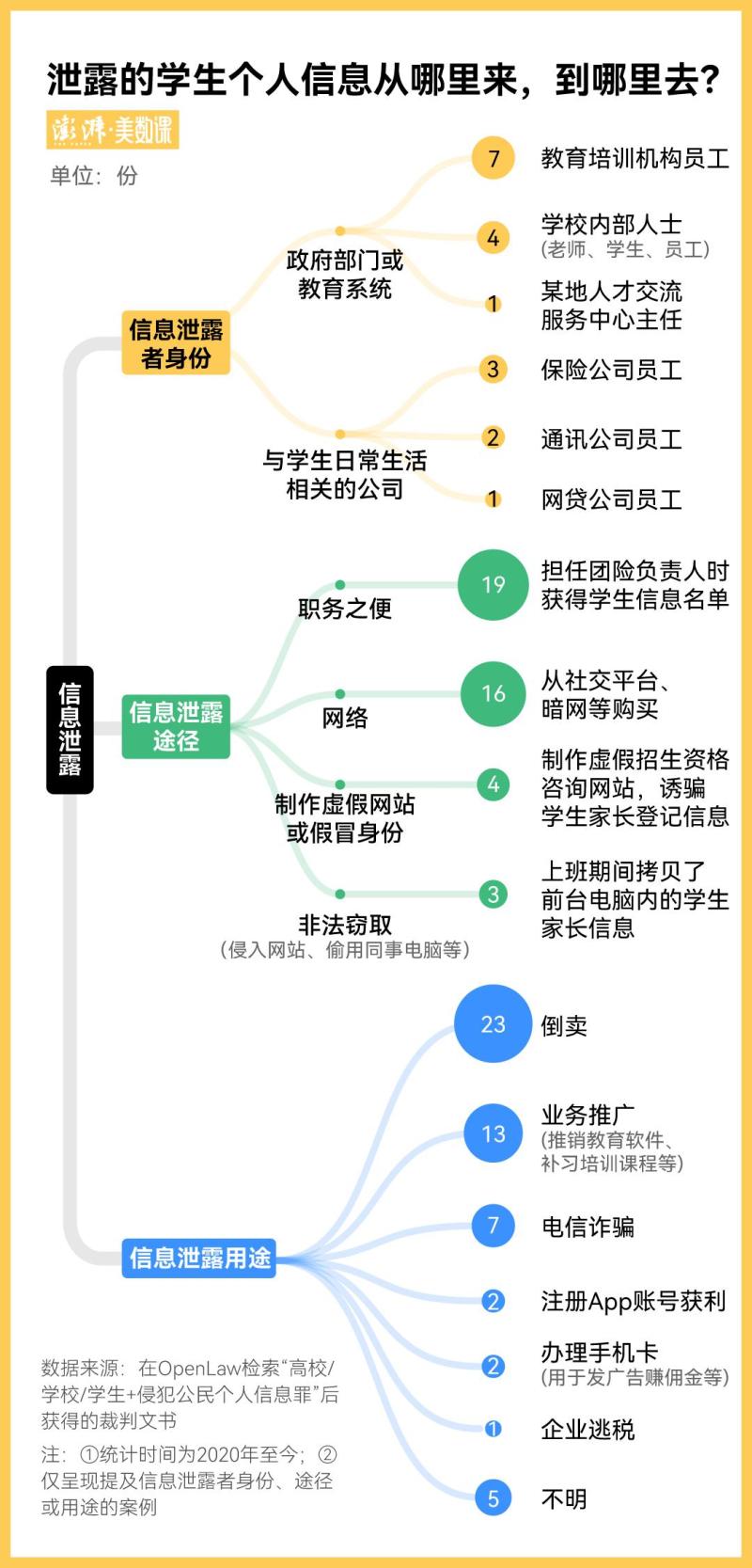
The responsibility for personal information leakage among students is usually attributed to individuals and does not fall on the company. Among the 52 relevant documents, only two cases are where the company is responsible for personal information leakage, while the other 50 cases are where individuals bear responsibility.
A document ruling that the company is illegal mentions that the legal representative of an education consulting company purchased over 270000 pieces of student information online and hired others to use this information to promote educational software through phone calls, free door-to-door teaching, and other means. The company profited at least 60000 yuan from this. The final court ruled that the company and its responsible persons committed the crime of infringing on the personal information of citizens, and imposed a total fine of 140000 yuan.
In the current incident of information leakage among students at the National People's Congress, Ma Ce, founding partner of Zhejiang Kenting Law Firm, believes that Ma may constitute the crime of infringing on personal information of citizens, while the school generally does not constitute the crime of infringing on personal information of citizens because there is no "criminal agreement" between the school and the students.
"Generally speaking, it is necessary to comprehensively consider whether the criminal act is committed for the benefit of the unit, whether it is carried out in the name of the unit, whether it has been decided by the unit, whether the illegal gains belong to the unit, and whether the unit knows and should know whether the enterprise and other units constitute a crime." Ma Ce sued Pengpai News, but if a school violates its information network security management obligations and refuses to correct after being ordered by regulatory authorities to take corrective measures, resulting in the leakage of personal information of its citizens, it may be convicted and punished for the crime of refusing to fulfill its information network security management obligations.
However, laws and regulations such as the Data Security Law and the Personal Information Protection Law impose necessary legal obligations on operating units. Ma Ce said that enterprises and other units should develop and implement data compliance systems internally, take necessary organizational and security measures, such as setting up an information security department and designating a person in charge of personal information protection. In addition, enterprises and other units should also cultivate employees' awareness of data compliance, clarify the red line for violations, in order to isolate or reduce the probability of criminal involvement among employees.
In large-scale information leakage incidents, Ma Ce suggests that users directly report to the police, especially when personal information is still facing the risk of expanding leakage, and enterprises and other units have an obligation to notify users. "Currently, few enterprises will implement notices, which will undoubtedly affect the timing of users taking protective measures.".




