Who is the mastermind behind the scenes? Expert Analysis: Wuhan Earthquake Monitoring Center Has Been Attacked by Overseas Cyber Attacks Countries | Cyber Attacks | Behind the Scenes
Earthquake intensity data or theft seriously endangers national security
Yesterday, the Jianghan Branch of the Wuhan Public Security Bureau in Hubei Province issued a police report stating that some of the network equipment at the front-end stations of the Wuhan Earthquake Monitoring Center's earthquake rapid report data collection points has been subjected to network attacks, and related earthquake intensity data is highly likely to be stolen, posing a serious threat to China's national security. Who initiated this cyber attack? Why did hacker organizations target the Wuhan Earthquake Monitoring Center? What is the true purpose of this cyber attack?
According to the police report released by the Jianghan Branch of Wuhan Public Security Bureau yesterday, the equipment of Wuhan Earthquake Monitoring Center has been implanted into backdoor programs by hacker organizations, posing a serious threat to China's national security.
It is understood that the Wuhan Earthquake Monitoring Center Station is managed by the Hubei Provincial Seismological Bureau and includes six monitoring stations, including Wuchang, Yingcheng, Macheng, Huangshi, Huangmei, and Jiugongshan. It mainly carries out business work and scientific research activities such as earthquake prediction and early warning, earthquake disaster risk prevention and emergency response. According to the police report from the Jianghan Sub bureau, after the Wuhan Earthquake Monitoring Center was attacked by a network, the seismic intensity data collected by the earthquake rapid report front-end station is highly likely to be stolen.

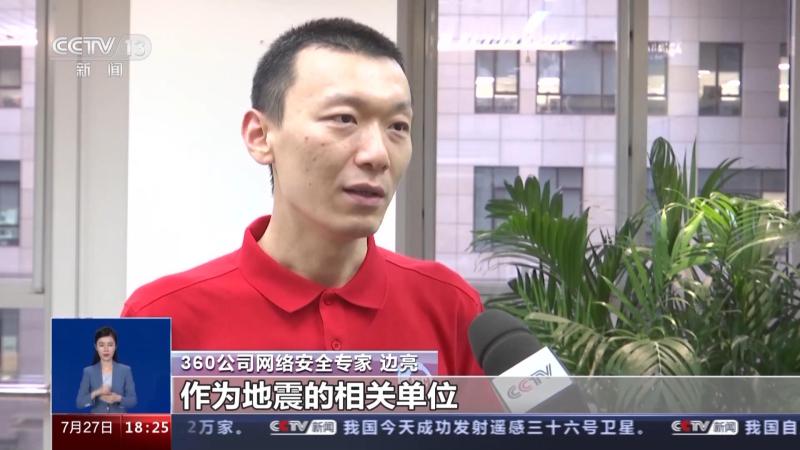
360 Company's cybersecurity expert Bian Liang: As an earthquake related unit, it must have research information or data related to the surface. If these important data are stolen, it may be possible to speculate whether the geological and water conditions in certain areas are suitable for deploying military facilities, or whether there are such cavities below the surface, suitable for deploying military facilities or equipment.
It is understood that seismic intensity data refers to the intensity and magnitude of an earthquake, which are two important indicators for measuring the destructive power of an earthquake. Especially, seismic intensity represents the degree of geological damage, and the higher the intensity, the greater the destructive power. According to experts in the field of earthquakes, seismic data is currently the most effective means of detecting underground spaces.
Evidence shows that the mastermind behind the scenes originated from US intelligence agencies
The Wuhan Earthquake Monitoring Center has been attacked by overseas cyber attacks, and experts have concluded that this is likely a cyber attack aimed at military reconnaissance. So who exactly launched this attack? According to the police report from the Jianghan Branch of the Wuhan Public Security Bureau, the cyber attack on the Wuhan Earthquake Monitoring Center was carried out by a foreign hacker organization with government background. A large amount of evidence obtained by the investigation team jointly established by the National Computer Virus Emergency Response Center and 360 Company also shows that the mastermind behind the network attack on the Wuhan Earthquake Monitoring Center came from American intelligence agencies.
It is understood that in recent years, the National Security Agency, the Central Intelligence Agency and other intelligence agencies of the United States frequently launch cyber attacks against relevant sensitive institutions in China. Their cyber weapons use extremely strict technical specifications for espionage. Various attack methods echo back and forth and link up with each other. Now they have covered almost all Internet and Internet of Things assets in the world. They can control other countries' networks at any time and anywhere and steal important and sensitive data from other countries.
In May this year, the National Computer Virus Emergency Response Center and 360 Company jointly released an investigation report, revealing the use of cyber attacks by the Central Intelligence Agency in other countries. The report shows that during the investigation of multiple typical cyber attack incidents in China, the joint investigation team captured and successfully extracted a large number of Trojan programs, feature plugins, and attack platform samples closely related to the Central Intelligence Agency from the information network of the victim units. These related cyber weapons have undergone extremely strict standardization, procedural and professional software engineering management, and currently only the Central Intelligence Agency of the United States strictly adheres to these standards and regulations in developing cyber attack weapons.
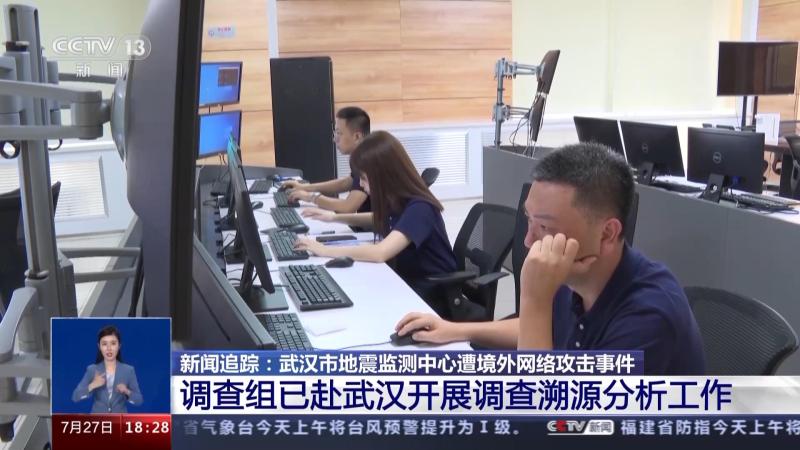
The investigation team of relevant departments has gone to Wuhan to conduct investigation and traceability analysis on the network attack behavior suffered by the Wuhan Earthquake Detection Center.
Du Zhenhua, Senior Engineer of the National Computer Virus Emergency Response Center: The current intelligence agency system in the United States has 18 major intelligence agencies. In addition to the Central Intelligence Agency and the National Security Agency, the Defense Intelligence Agency, National Geospatial Intelligence Agency, and National Reconnaissance Agency, all of which belong to the United States Department of Defense, have strong analytical capabilities for military, geographic, and geological intelligence information. Therefore, we cannot rule out the possibility of multiple intelligence agencies cooperating to carry out this attack.

Link: Northwestern Polytechnical University is under cyber attack by the US NSA
According to cybersecurity experts, data has become a fundamental strategic resource for a country, especially the large amount of core and important data related to national politics, economy, diplomacy, military, etc. contained in key infrastructure. Data security is related to national security. In order to obtain these important data from our country, American intelligence agencies frequently launch cyber attacks on relevant universities, important government agencies, etc. in our country. Last year, Northwestern Polytechnical University suffered from overseas cyber attacks, which originated from a specific intrusion operations office under the National Security Agency of the United States.
In September last year, the National Computer Virus Emergency Response Center of China and 360 Company jointly released the "Investigation Report on Northwest Polytechnical University's Network Attack by the US NSA". The report showed that the specific intrusion action office under the National Security Agency of the United States had strong targeted network attack techniques and tactics against other countries, adopting a semi-automatic attack process, single point breakthrough, gradual infiltration, and long-term theft.
The technical team discovered that a specific intrusion action office under the National Security Agency of the United States has been carefully prepared for a long time, using the "Sour Fox" platform to carry out man in the middle hijacking attacks on internal hosts and servers of Northwestern Polytechnical University, deploying "Anger Jets" remote control weapons, and controlling multiple critical servers.
The report shows that a specific intrusion action office has obtained a batch of network boundary device account passwords, business device access permissions, router and other device configuration information, as well as FTP server documentation information, by stealing key sensitive data such as account passwords, operation records, and system logs from remote business management personnel of Northwestern Polytechnical University.
The technical team, based on the characteristics of specific intrusion action office attack links, penetration methods, Trojan samples, and other factors, identified illegal attacks infiltrating infrastructure operators within China. They constructed a so-called "legitimate" channel for remote access to the core data network of infrastructure operators, achieving penetration control over Chinese infrastructure.
How to protect against increasingly severe network security threats?
How should relevant government agencies and departments take corresponding protective measures as network security threats become increasingly severe? Let's listen to the analysis of 360 Company's network security expert Bian Liang.





